Secure Your API Endpoint using Low-code with BuildShip
As you build, ship, and deploy workflows on BuildShip, securing your API endpoints is crucial when exposing them to the internet. Ensuring proper authentication and validation of requests protects your application from unauthorized access and potential vulnerabilities. In this guide, we’ll walk you through how to secure your API endpoints using low-code workflows in BuildShip.
Why Securing API Endpoints Matters While Building Your Workflows
APIs are the backbone of modern applications, facilitating data exchange and communication between services. However, exposing an API endpoint to the internet can make it vulnerable to malicious requests and data breaches. By implementing proper authentication mechanisms, such as the Authorization header, you can ensure that only valid clients gain access to your application’s resources.
Using the Authorization Header for Secure Workflows
The Authorization header is a standard method for passing authentication information to the server. It typically includes a token or credentials that the server uses to:
- Validate the client’s identity.
- Grant or deny access to the requested resource.
BuildShip makes it simple to incorporate the Authorization header into your workflows. You have two options to access and utilize it:
Option 1: Listening for the Authorization Header from a Request
Follow these steps to listen for the Authorization header directly in your workflows:
1. Send a Request with the Authorization Header:
Send a request to your workflow endpoint, including the Authorization header.

2. Load the Request Data in BuildShip
In BuildShip, click the Get Data button to load the request data. Once loaded, expand the list of available headers to locate the Authorization header.

3. Add the Authorization Header to the Input Schema
Click on the Add input to schema button to include the Authorization header as an input for your workflow.

And that’s it! The Authorization header is now part of your workflow’s input schema.
Option 2: Manually Accessing the Authorization Header
If you prefer manual configuration, follow these steps:
1. Set Up the REST API Trigger
Click the Connect button at the top of your workflow to set up the REST API Trigger.
2. Add a New Input for the Authorization Header
Under the Workflow Inputs Schema section, add a new input, name it “Authorization,” and set its type to String. Save the input.

3. Use Dot Notation to Access Header Values
Update the input to select the Authorization header from the request headers using dot notation:
Body > Trigger Data > headers > headers.

Validating the Authorization Header
To enhance security, validate the Authorization header using a Branch Node:
1. Add a Condition to Validate the Header
- Select the Authorization input created earlier as the first value of the condition.
- Use the “equals to” operator (==) for comparison.
- Set the final value to the token or key you want to validate.

2. Organize Workflow Nodes
Place workflow nodes into the “then” and “else” branches based on whether the header is valid or invalid.
Returning Authorized and Unauthorized Responses
After validating the Authorization header, configure your workflow to return appropriate responses:
1. For Authorized Requests
Return an HTTP 200 (OK) response.
2. For Unauthorized Requests
Return an HTTP 401 (Unauthorized) response. Use the Output Node to set the status code and response body:

Lastly, you can update the workflow output properties in the trigger settings to return the Flow Output for the response body and the Flow Output Status Code for the response status code.

For setting the Response Body, select Flow Output > Flow Output
For setting the Response Status Code, select Local Variables > Flow Output Status Code
Testing Your Secured API Endpoint
With these measures in place, your workflow is now secured. Test your endpoint to ensure it behaves as expected, allowing only authorized requests to pass through.
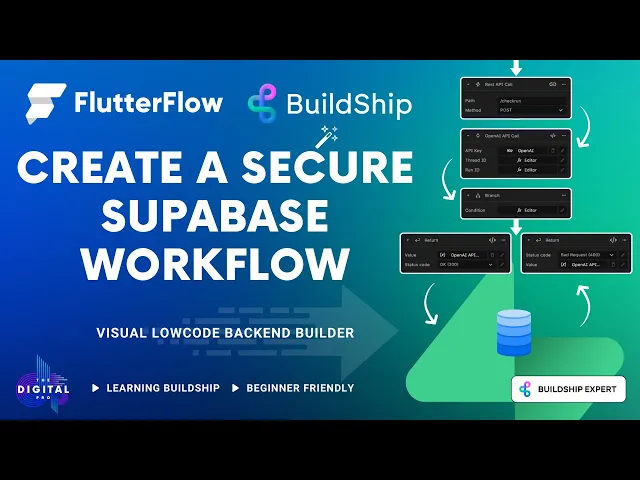
Final Workflow Structure
Your secured workflow should look similar to this:

Additional Resources for Database Integration
For Supabase Users
If you’re using Supabase, check out the video below to learn how to build a secure application from scratch.
For Firebase Users
For Firebase integration, refer to our Firebase Authenticated User Trigger documentation for easy setup.
Conclusion
Securing your API endpoints doesn’t have to be complex. With BuildShip’s low-code platform, you can easily implement robust authentication mechanisms using the Authorization header. Start building and shipping workflows with confidence, knowing your endpoints are safe from unauthorized access.
Ready to secure your workflows? Sign up here.






